Cable Modem Hacking
For better quality, you can Download this Video in HD
 Today Facebook is one of the largest social networking websites, with more then 500 million active users, so why not to make some money while “wasting” your time there. Facebook is a great money making opportunity
Today Facebook is one of the largest social networking websites, with more then 500 million active users, so why not to make some money while “wasting” your time there. Facebook is a great money making opportunity
The author of this book is Stella Demin. This book is a great source for the beginner who want to make money. It’s written in such a manner that even a 5th grade kid can understand it.
This book costs $5. By buying this book you are also making a donation to this blog.
![]()
Bonus E-Book: Farmville Secrets – The Best Kept Secrets Revealed
I get a lot of emails where my readers are asking for help to find out if his/her partner is cheating on them, chatting to someone she/he shouldn’t be, etc. So here i decided to answer this question, and to get it clear once for all.
Except the advantages of using a RAT, there are also few disadvantages that you should know about:
1. The RATs are detected by the most anti-virus software.
2. You can get infected by using a RAT.
3. You can get traced when you rat somebody.
In this article i am going to share A step by step guide that allows you to remotely access anybody’s webcam, microphone, files and desktop from anywhere in the world, without to worry about the things i mention above.

You can install this on any PC and monitor who ever uses that PC, or even someone passing by. There are no system requirements and this works 99.9% of the time.
This also includes the ability to:
This software costs $14.99, but I think the price totally worth for a software like this one.
I have tested this from every single angle possible and have had the BEST success rate with it.
 Many people think that a computer can only be infected by directly downloading a file, which is completely wrong. People also think, just having an anti-virus, means they will never become infected. The internet can be one of the best places, yet one of the worst. Considering malware is becoming more and more advanced daily (becoming undetectable, hiding under legitimate process names, disguising as Java applets or ActiveX components, etc.) We need to be on our toes to prevent the chances of becoming infected. I will be covering safety tips to keep your computer safe from infections.
Many people think that a computer can only be infected by directly downloading a file, which is completely wrong. People also think, just having an anti-virus, means they will never become infected. The internet can be one of the best places, yet one of the worst. Considering malware is becoming more and more advanced daily (becoming undetectable, hiding under legitimate process names, disguising as Java applets or ActiveX components, etc.) We need to be on our toes to prevent the chances of becoming infected. I will be covering safety tips to keep your computer safe from infections.
Download an Anti-Virus
An anti-virus or an ‘AV’, is a type of software that is used to find, protect, and remove malware. Many of the newest anti-virus software comes with great web protection, which can be vital to ensure your safety online. AV’s with web protection can help you by warning you how safe a website is. Although you don’t need an anti-virus to protect you online, it is recommended you do have one to ensure maximum safety. Most companies that make AV’s typically have different packages depending on the security and extra features, such as; Avast!, Kaspersky, and AVG. Of course, if you buy the Internet Security packages of these AV’s, your protection online will be substantially better. Be sure to have only one anti-virus running at one time.
Download a Firewall
A firewall is a piece of software that is an essential part of your protection online. It can prevent DDoS/DoS attacks, it can prevent a hacker from infiltrating your network, shares your privacy to a greater degree, etc. Below is a list of a few, great firewalls. All have been recommended by numerous people.
Avoid Java Drive-By’s
What is a Java Drive-by?
A Java Drive-by is a download, but it disguises itself to be a Java applet, or an ActiveX component, and is installed without the user’s notice. The drive-by usually occurs once you open a web page.The user would see that a pop-up would ask them to ‘Run’ or ‘Cancel’. The normal user would typically click ‘Run’, because it they might think the clicking ‘Run’ would continue onto the web page, in actuality, they have just been infected by a malicious file.
Example of what a Java drive-by could possibly look like:
There are a few ways you can do this.
Avoid Torrents and Other Downloads
Why avoid torrents, when you can get all the music you want, for free? Because some files in torrents might be binded to other files; namely a form of malware. It’s okay to use torrents, but be careful with what you download, and always try to download from a trusted user. Same thing goes for regular downloads, this includes; games, movies, music, pictures, etc. For example, you see a program online you like, and you don’t want to pay for it, it’s possible it can be infected. Be hasty when downloading, it can be binded with a malware. Before downloading any type of file off the internet, please read the comments about the download if there are any. It could be the thing that prevents you from getting infected. In no way, shape, or form, am I saying stop using torrents, and downloading offline, just be careful.
Media files (ie. .mp3, .avi., .jpg, etc.) that are binded with malware can be easy to spot if you’re good with computers. If a media file was binded with malware, it would be called something along the lines of; Songname.mp3.exe or Songname.mp3.com. If you see ‘.com’ or ‘.exe’ in a media file, steer clear of that file, and remove it from your computer immediately.
How To Check if a File is Actually Infected
Avoid Phishers
‘Phishing’ is the technique of stealing user names and password through a fake log-in page. The fake log-in page tends to look similar, if not, identical to the original page. If you enter your information into the illegitimate log-in page, the log-in info you used will be sent to the hacker, without your knowledge of this happening.
Tab-Nabbing
Recently, there has been a new type of a phishing attack discovered. It is called ‘tab-nabbing’. Here’s what it does: Say you log into Facebook, and you need to open a new tab for whatever reason. Once it is detected you are away from the web page, the ‘tab-nabber’ changes the ‘favicon’ of the web page (in this case, Facebook.) It then typically redirects you from the page, and asks you to log into the page again. You normally wouldn’t think it could be harmful to you at the moment, because you see the ‘favicon’ and you think you’re logging into the original website.
How to Prevent Falling Victim to a Phisher
Clear Your Cookies
An HTTP cookie, or more commonly known as a ‘cookie’ is a form of text that is stored into the user’s web browser. A cookie can be used for authentication or anything else that is completed through storing data. You can clear your cookies and cache either through your web browser, or using a program such as; ATF Cleaner. The more cookies you have stored, there’s higher possibility your internet will run slower. Cookies are not malicious in any way, as they cannot execute themselves. Although, they can be used as spyware, because cookies can track what you do online, and can be used to invade your privacy, or even cause malware related problems in the future.
Ways To Avoid Cookies
You can easily avoid cookies by modifying a few settings in your web browser.
Tools > Internet Options > Security Tab > Set security level to “High”, or Custom level > Cookies > Disable.
Tools > Options > Privacy > Cookies > Remove the check next to the “Allow sites to set cookies” option.
How To Clear Your Cookies
You can easily clear your cookies, either through a program such as CCleaner
Click on Tools button > Click on ‘Choose Recent History’ > Make sure the ‘Cookies’ box has a check mark next to it > Click the ‘Clear Now’ button.
Click on Safety button > Click on ‘Clear Browsing History’ > Make sure the ‘Cookies’ box has a check mark next to it > Click the ‘Delete’ button.
Click on the ‘wrench icon’ on the toolbar > Click ‘Clear Browsing Data’ > Place a check mark next to ‘Delete Cookies’ > Click the ‘Clear Browsing Data’ button.
Other Security Tools
My final advise is to use your common sense when it comes to browsing the internet. Many people run their computers and surf the internet without an anti-virus, because they tend to know what’s legitimate, and what is not, and always take caution in what they do online.
So if some of you may have heard, Graboid offers free movies, TV shows and more to download. It is subscription based on bandwidth. In this post i am going to show you how to download as much as you want videos, movies, and TV shows through Graboid for free.
First, download the program HERE.
Then after you open the program you will have the option to create and account.

Create it and log in. You will notice your bandwidth restriction, and your account will expire in a month, when you have to buy a subscription.

Once your account has expired, I have discovered a new way to make accounts (NOTE: After your account is created, you will never be able to create a free account again, nor through the program or website).
Make this batch script:
cd %appdata%
del MozillaControl /F /q
cd “%LOCALAPPDATA%\Graboid_Inc\”
del *.* /F /q
Or download it HERE if you don’t know how.
Run the batch file, and behold, the new account button shall appear again. Enter a different email address than previous, and your good to go.
For those with issues creating accounts:
1. Renew your IP address (unplug your modem for about 5mins and then reconnect it).
2. If the problem is not solved by number 2, download Hotspot Shield HERE
3. If it still doesn’t work, wait a week. This will give a chance for your ISP to reset your IP.
Hope this helped!
An ultimate hack which enable u to trace any one any where in the world
 Most of you may be curious to know how to find the IP address of your friend’s computer or to find the IP address of the person with whom you are chatting in Yahoo messenger or Gtalk. Finding out someone’s IP address is like finding their phone number, an IP address can be used to find the general location where that person lives. Now while most of the tutorials on the net teach you how to steal an ip address via MSN, or any other chat software, in this post I’ll show you how to find IP address of someones computer using script. Using this method for hacking someones ip adress is very easy and effectively, so just follow the steps bellow.
Most of you may be curious to know how to find the IP address of your friend’s computer or to find the IP address of the person with whom you are chatting in Yahoo messenger or Gtalk. Finding out someone’s IP address is like finding their phone number, an IP address can be used to find the general location where that person lives. Now while most of the tutorials on the net teach you how to steal an ip address via MSN, or any other chat software, in this post I’ll show you how to find IP address of someones computer using script. Using this method for hacking someones ip adress is very easy and effectively, so just follow the steps bellow.
NOTE: This tutorial is for educational purposes only, I am NOT responsible in any way for how this information is used, use it at your own risk.
How to Hack Someones IP Address?
Alright, I’m gonna give you this script, that you write in the index.php. It will redirect them to http://www.google.com/, but you can change that in the script.
Here is the sript:
Code:
<?php
$file = ‘IPz.txt’;
$handle = fopen($file,’a’);
if(!isset($_GET[‘p’])) { header(‘Location: http://google.com’); }
fwrite($handle, $_GET[‘p’].’: ‘.$_SERVER[‘REMOTE_ADDR’].’\r\n’);
fclose($handle)
?>
1. First of all you need to make a new .txt document on the website you’re uploading this to. Call it IPz.txt (You can change that in the script aswell where it says $file = ‘IPz.txt’; in the second line. Then change the CHMOD to 777.
2. Now you need to past the script above in to a .php document, and upload it.
3. Now you make people visit your site, and they will get redirected to Google.
4. To view the IP, you simply add “/IPz.txt” after your domain, and you’ll see the IP.
This is a very simple, but effectually method for stealing someones IP Address.
Hope you’ll find this tutorial useful. Happy Hacking 🙂
Finding out someone’s IP address is like finding their phone number, an IP address can be used to find the general location where that person lives. If you can email the person, or get them to click a link on a forum, you can find out their IP easily.
1. Surf to www.whatstheirip.com. The site will ask for your email. Enter your email and click “get links”.
2. You will be emailed a couple links. The links when clicked will lead to a “page not found” and “invalid thread specified”. When one of the links is clicked it will email you back the IP of whoever clicked the link.
3. If its a victim that I have interaction with on a board or forum I always ask them “Is this you they are referring to in this thread”….the person invariably clicks the link and I’m emailed back their IP
Now of course once you have someones IP you can remotely shut down their computer or port scan them or whatever your deviant mind can think of.
Step 2: Search on the internet for a picture you like. Save it to C:\Hide. Change the name to a easy one, like picture…
Step 3: Open C:\Hide and select all your files, Right click > Add to Archive. All your files will be put in a rar file. Now rename the rar file to a easy one like Hide.rar
Step 4: Open the command prompt.
Execute this: cd C:\hide
Then this: copy /b nameofthepicture.jpg + Hide.rar nameofthepicture.jpg
If you did everything hide the command prompt should return:
1 File(s) Copied or something.
Step 5: What did we do?
We copied all our files into a picture. Now try opening the picture by double clicking on it. It will open Windows Image viewer or something, so you will see the picture.
How to see your files?
Open winrar from the start menu, and navigate the C:\hide and double click (in winrar) on the picture. You should see your files now.
1. Open Firefox.
2. Clear your cache.
Open Firefox and select “Tools” -> “Options”, select the Advanced panel, and click on the Network tab. In the Offline Storage section, click Clear Now.

Click OK to close the Options window
3. Load the web page that contains your flash video. Make sure it streams all the way. This means you now have it in your computer’s cache.
4. Open a new tab and write “about:cache” in the address bar (without the “quotes”).

5. Under “Disk cache device”, copy the path shown for the cache directory.
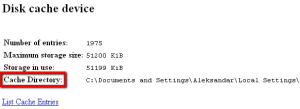
6. Paste that path in My Computer, or navigate to it however you want.
7. Order files by size.
8. The biggest file should be your video. It’s going to have a weird name like 54DDEA30e01 but that’s fine. This is your video.
9. Open the file with a media player that supports the format, such as VLC Player.
NOTE: Most likely, your computer won’t know which software to run this file type with, so just select “open file with” option after clicking the file with the secondary mouse button, and choose VLC Player.
I’ve been writing a lot about trojans, and keyloggers on this blog. It’s very simple to make a trojan/keylogger, but to make it undetectable by the antiviruses is the hard part. Nowadays crypting trojan don’t give a good result if you use use a public crypter, otherwise you need to buy a private edition or to hex it. Here i am going to show you how to make your trojan, keylogger, or RAT almost FUD (Fully Undetectable) by any anti-virus software.
We gonna need a Privacy Protection Software. This kind of software is used by program creators to protect their creation from cracking and reverse engineering. We gonna do the same to a trojan and you are going to see the result.
1. First of all you need to download the program: PC Guard for Win32
2. Open the program, and in the “Application filename” browse your server’s location.

2. Click on the “General” tab, and check the options like on the image below.

3. Now do the same with the “Security & Encryption” tab. Look at the image below to see what options to check.

4. At the end choose “Protection Methods”, and select the following options:
The Scan Results:
Poison Ivy server:
Do you have questions, comments, or suggestions? Feel free to post a comment!